
Prerequisites:
An Ubuntu 20.04 machine connected to the internet.
Download and install the latest Debian Ejabberd Community Server package from here:
www.process-one.net/en/ejabberd/downloads/
shell
wget https://www.process-one.net/downloads/downloads-action.php?file=/20.07/ejabberd_20.07-0_amd64.deb
you may have to rename the downloaded file to ejabberd.deb.
Issue:
shell
dpkg -i ejabberd.deb
Generate a CSR and get it publicly signed. You can get many SSL/TLS brands right from www.ssltrust.com.au
Ejabberd expects a single certificate file concatenating the base64 encoded public key underneath the private key. If you have them in separate files, you can issue the following command to construct the bundle ejabberd is looking for:
shell
cat key.pem cert.pem >> bundle.pem
(CD into the directory ejabberd was installed into)
Setup ejabberd as a system service:
shell
cp ejabberd.service /etc/systemd/system systemctl start ejabberd
Next we’ll visit the web interface. It can be hit over SSL/TLS using a self-signed certificate on port 5443. For example, I would visit https://xmpp.schattenconsulting.com:5443/admin
Check the file /opt/ejabberd/conf for the default username (admin@hostname). The default password is admin. It is recommended to change this default password for production usage.
Ejabberd ships with a self-signed certificate which we will be replacing with our publicly signed cert. Ejabberd previously used explicit SSL/TLS to secure communications, but chats are now secured via StartTLS. StartTLS is a method of employing SSL/TLS whereby a connection starts off in the clear, and SSL/TLS is invoked by the client at the beginning of the conversation.
Next we will provision our first user. From the web interface, navigate to your virtual host (named the same as your machine’s host name) and select “Users”.
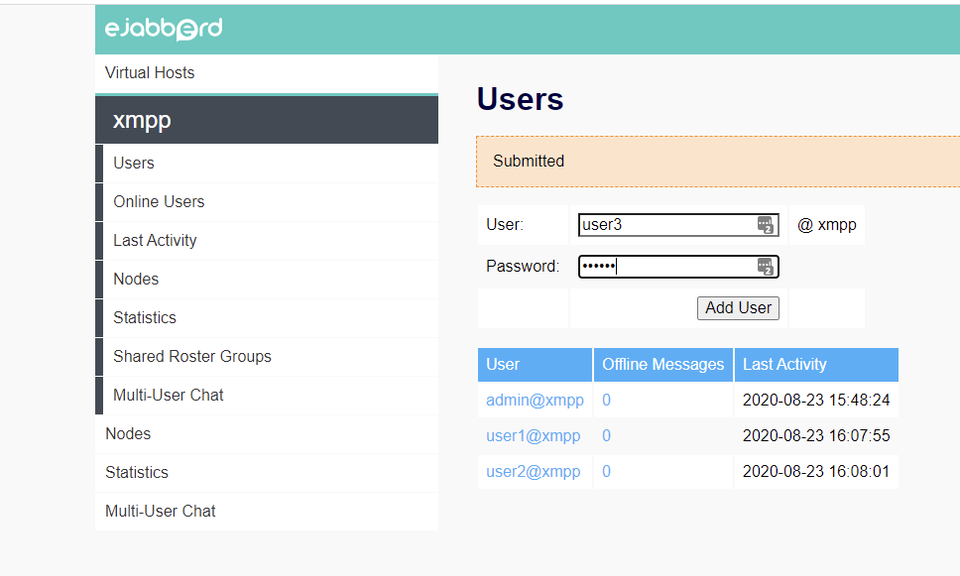
Create at least one user. Note that ejabberd supports LDAP (including Microsoft’s Active Directory) for authentication, but that is beyond the scope of this guide.
Move your bundle.pem file into the conf directory under /opt/ejabberd.
Back in the ejabberd.yml file, locate the line "certfiles:" and replace with your bundle containing the publicly signed certificate.
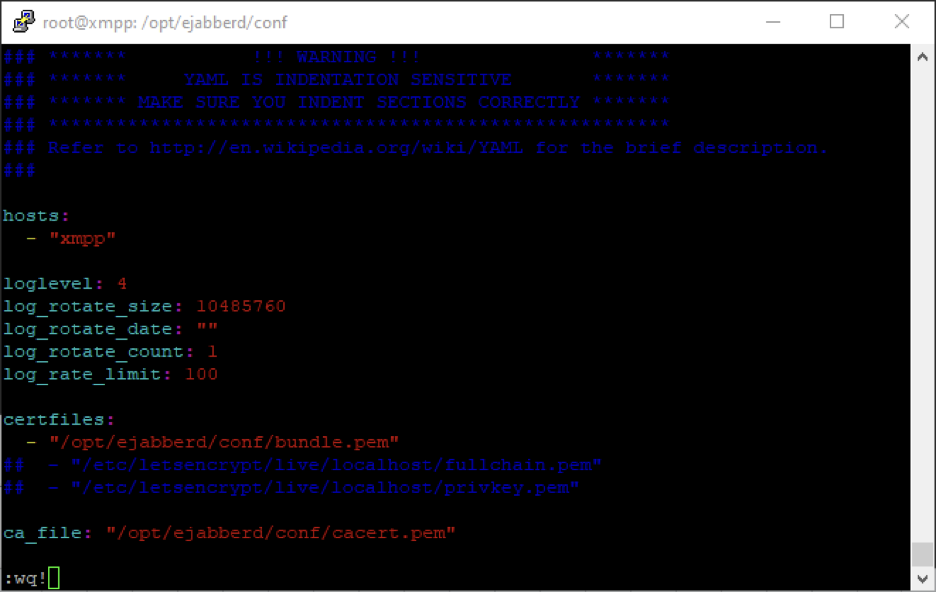
Issue:
shell
systemctl restart ejabberd
to restart the service.
Now we can download and install the Pidgin IM client. www.pidgin.im/install/
After installing Pidgin, select Add.
Under Protocol, selecting XMPP will bring up the following options:
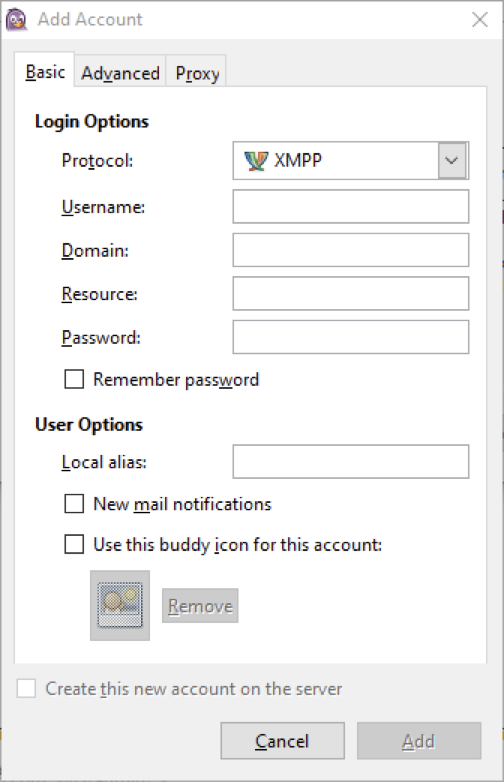
Username: Corresponds to JUST the username created in the Ejabberd admin interface.
Domain: Corresponds to the name of the virtual host in the Ejabberd admin interface
Resource: Corresponds to the name of the plaintext port (5222). StartTLS will be used for encryption.
Password: The password of the user, specified in the Ejabberd admin interface.
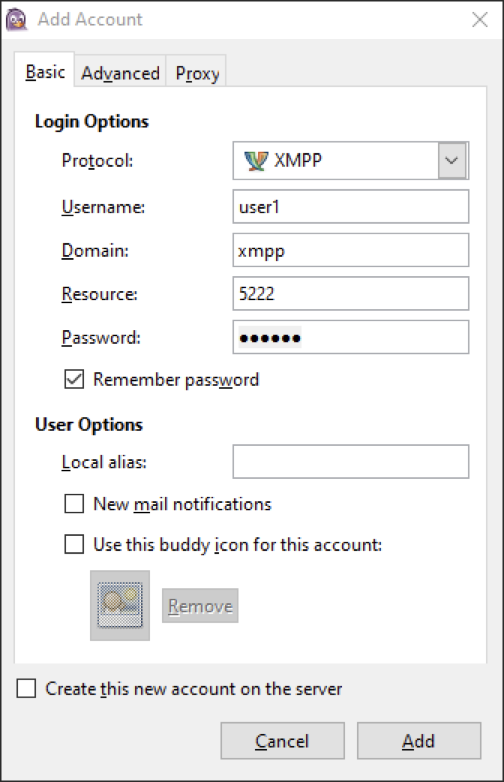
Now, navigate to the Advanced tab.
By default “Connection Security” will be set to “Require Encryption”. Leave this secure default, as we have already setup SSL/TLS!
Under Connect Server enter the FQDN of your XMPP server.
Select Add.
Pidgin lives in your task bar. Right click on its icon, and select New Message.
Enter the handle of a user on the same virtual host you wish to communicate with.
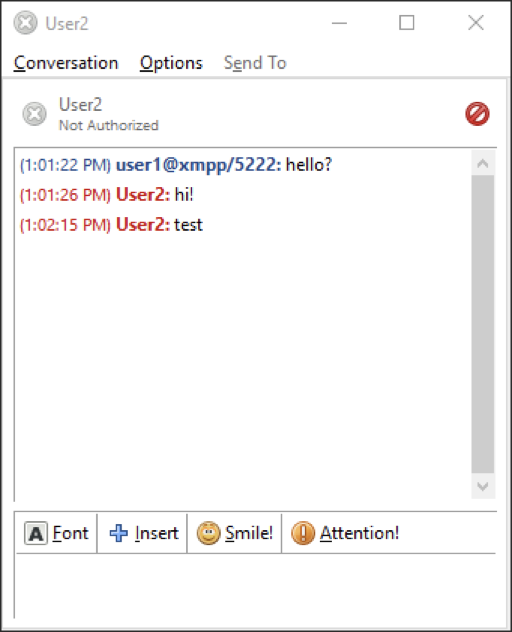
This communication is secured via SSL/TLS in transit due to the use of StartTLS.
Ejabberd can be highly customized through the use of modules. Modules exist for things like logging all chats that pass through the server to a SQL database. This is useful for administrators who need to maintain access to user communications for compliance reasons. There are also plugins for allowing users to browse their IM history via a web interface, supporting file transfers, and even handling audio/video calling.
Discussions and Comments
Click here to view and join in on any discussions and comments on this article.

